1 Introduction to the Spring Security REST plugin - Reference Documentation
Authors: Alvaro Sanchez-Mariscal
Version: 1.4.0
1 Introduction to the Spring Security REST plugin
The Spring Security REST Grails plugin allows you to use Spring Security for a stateless, token-based, RESTful authentication.This plugin depends on Spring Security Core 2.x. Make sure your application is compatible with that version first. There is a feature request, that may be addressed in the future if there is enough community interest / love :)The default behaviour of Spring Security is to store the authenticated principal in the HTTP session. However, in a RESTful scenario, we need to make sure our server is stateless.If you are writing an API that will be used by other programs, you can use OAuth for this. But if you are exposing your API for a front-end Javascript client to implement a Single Page Interface, OAuth is not an option, specially if you want to authentication end users against your own user backend (eg: LDAP). In this case, a token-based authentication may be a more suitable implementation, like the following:
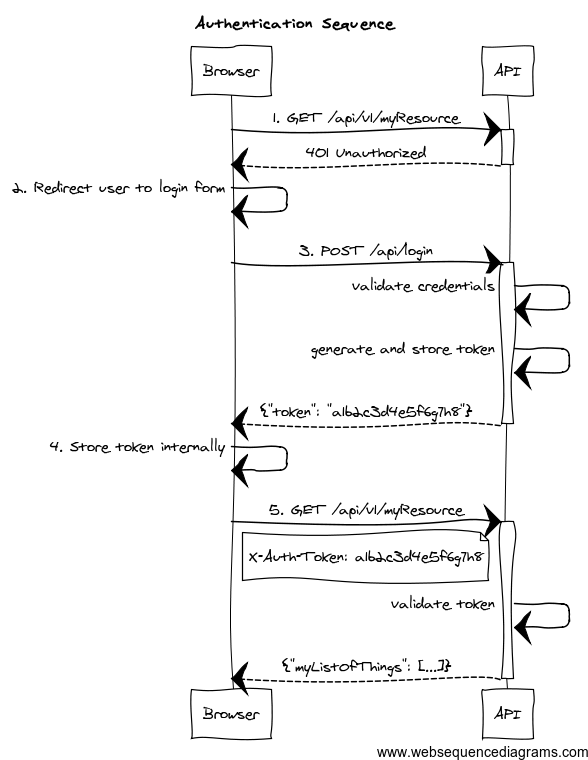
- The client application requests and endpoint that requires authentication, so the server responds with a 401 response.
- The client redirects the user to the login form.
- The user enter credentials, and the client sends a request to the authentication endpoint. The server validates credentials, and if valid, generates, stores and sends back a token to the client.
- The client then stores the token internally. It will be sent on every API method request.
- The client sends again a request to the protected resource, passing the token as an HTTP header.
- The server validates the token, and if valid, executes the actual operation requested.
Release History
- 12 August 2014
- 14 July 2014
- 4 July 2014
- 24 June 2014
- 24 June 2014
- 20 June 2014
- 11 June 2014
- 1 June 2014
- 29 May 2014
- 23 April 2014
- 16 April 2014
- 3 April 2014
- 18 March 2014
- 4 March 2014
- 17 February 2014
- 10 February 2014
- 4 February 2014
- 31 January 2014
- 15 January 2014
- 14 January 2014
- 13 January 2014
- 12 January 2014
- 10 January 2014
- 1.0.0.RC2
- 31 December 2013
- Initial 1.0.0.RC1 release.